Visits: 3132
sometimes you cannot use SES, But the users still want their messages delivered. so here is some info. I hope that it is helpful.
I’ve been trying to setup my hmailserver with DKIM.
Unfortunatly our Windows HmailServer is now depricated.
To start installing the replacement with Postfix, Dovecot, Postgres, Letsencrypt certificate and Roundcube, launch the Complete Email Server with Webmail in the AWS Cloud.
I was following this guide -> https://www.hmailserver.com/forum/viewtopic.php?t=29402
And I created my keys with this site -> https://www.port25.com/dkim-wizard/
Domain name: linnabary.us
DomainKey Selector: dkim
Key size: 1024
I created a pem file;
-----BEGIN RSA PRIVATE KEY----- <key> -----END RSA PRIVATE KEY-----Saved it and loaded it into hmailserver
When I set this up on NameCheap I selected TXT Record, set my host as @, and put this line in, minus key of course;
v=DKIM1; k=rsa; p=<KEY>Now when I test with -> http://www.isnotspam.com
It says my DKIM key is as follows;
---------------------------------------------------------- DKIM check details: ---------------------------------------------------------- Result: invalid ID(s) verified: header.From=admin@linnabary.us Selector= domain= DomainKeys DNS Record=._domainkey.I was wondering if I am making any obvious errors in my record.
Edit;
The email contains the following line;
dkim-signature: v=1; a=rsa-sha256; d=linnabary.us; s=dkim;This is what the setup looks like on NameCheap;
And here is the next test email from ;
This message is an automatic response from isNOTspam's authentication verifier service. The service allows email senders to perform a simple check of various sender authentication mechanisms. It is provided free of charge, in the hope that it is useful to the email community. While it is not officially supported, we welcome any feedback you may have at . Thank you for using isNOTspam. The isNOTspam team ========================================================== Summary of Results ========================================================== SPF Check : pass Sender-ID Check : pass DKIM Check : invalid SpamAssassin Check : ham (non-spam) ========================================================== Details: ========================================================== HELO hostname: [69.61.241.46] Source IP: 69.61.241.46 mail-from: admin@linnabary.us Anonymous To: ins-a64wsfm3@isnotspam.com --------------------------------------------------------- SPF check details: ---------------------------------------------------------- Result: pass ID(s) verified: smtp.mail=admin@linnabary.us DNS record(s): linnabary.us. 1799 IN TXT "v=spf1 a mx ip4:69.61.241.46 ~all" ---------------------------------------------------------- Sender-ID check details: ---------------------------------------------------------- Result: pass ID(s) verified: smtp.mail=admin@linnabary.us DNS record(s): linnabary.us. 1799 IN TXT "v=spf1 a mx ip4:69.61.241.46 ~all" ---------------------------------------------------------- DKIM check details: ---------------------------------------------------------- Result: invalid ID(s) verified: header.From=admin@linnabary.us Selector= domain= DomainKeys DNS Record=._domainkey. ---------------------------------------------------------- SpamAssassin check details: ---------------------------------------------------------- SpamAssassin 3.4.1 (2015-04-28) Result: ham (non-spam) (04.6points, 10.0 required) pts rule name description ---- ---------------------- ------------------------------- * 3.5 BAYES_99 BODY: Bayes spam probability is 99 to 100% * [score: 1.0000] * -0.0 SPF_HELO_PASS SPF: HELO matches SPF record * -0.0 SPF_PASS SPF: sender matches SPF record * 0.2 BAYES_999 BODY: Bayes spam probability is 99.9 to 100% * [score: 1.0000] * 0.1 DKIM_SIGNED Message has a DKIM or DK signature, not necessarily * valid * 0.8 RDNS_NONE Delivered to internal network by a host with no rDNS * 0.0 T_DKIM_INVALID DKIM-Signature header exists but is not valid X-Spam-Status: Yes, hits=4.6 required=-20.0 tests=BAYES_99,BAYES_999, DKIM_SIGNED,RDNS_NONE,SPF_HELO_PASS,SPF_PASS,T_DKIM_INVALID autolearn=no autolearn_force=no version=3.4.0 X-Spam-Score: 4.6 To learn more about the terms used in the SpamAssassin report, please search here: http://wiki.apache.org/spamassassin/ ========================================================== Explanation of the possible results (adapted from draft-kucherawy-sender-auth-header-04.txt): ========================================================== "pass" the message passed the authentication test. "fail" the message failed the authentication test. "softfail" the message failed the authentication test, and the authentication method has either an explicit or implicit policy which doesn't require successful authentication of all messages from that domain. "neutral" the authentication method completed without errors, but was unable to reach either a positive or a negative result about the message. "temperror" a temporary (recoverable) error occurred attempting to authenticate the sender; either the process couldn't be completed locally, or there was a temporary failure retrieving data required for the authentication. A later retry may produce a more final result. "permerror" a permanent (unrecoverable) error occurred attempting to authenticate the sender; either the process couldn't be completed locally, or there was a permanent failure retrieving data required for the authentication. ========================================================== Original Email ========================================================== From admin@linnabary.us Wed Apr 12 17:41:22 2017 Return-path: <admin@linnabary.us> X-Spam-Checker-Version: SpamAssassin 3.4.0 (2014-02-07) on isnotspam.com X-Spam-Flag: YES X-Spam-Level: **** X-Spam-Report: * 3.5 BAYES_99 BODY: Bayes spam probability is 99 to 100% * [score: 1.0000] * -0.0 SPF_HELO_PASS SPF: HELO matches SPF record * -0.0 SPF_PASS SPF: sender matches SPF record * 0.2 BAYES_999 BODY: Bayes spam probability is 99.9 to 100% * [score: 1.0000] * 0.1 DKIM_SIGNED Message has a DKIM or DK signature, not necessarily * valid * 0.8 RDNS_NONE Delivered to internal network by a host with no rDNS * 0.0 T_DKIM_INVALID DKIM-Signature header exists but is not valid X-Spam-Status: Yes, hits=4.6 required=-20.0 tests=BAYES_99,BAYES_999, DKIM_SIGNED,RDNS_NONE,SPF_HELO_PASS,SPF_PASS,T_DKIM_INVALID autolearn=no autolearn_force=no version=3.4.0 Envelope-to: ins-a64wsfm3@isnotspam.com Delivery-date: Wed, 12 Apr 2017 17:41:22 +0000 Received: from [69.61.241.46] (helo=linnabary.us) by localhost.localdomain with esmtp (Exim 4.84_2) (envelope-from <admin@linnabary.us>) id 1cyMGg-0007x2-1Q for ins-a64wsfm3@isnotspam.com; Wed, 12 Apr 2017 17:41:22 +0000 dkim-signature: v=1; a=rsa-sha256; d=linnabary.us; s=dkim; c=relaxed/relaxed; q=dns/txt; h=From:Subject:Date:Message-ID:To:MIME-Version:Content-Type:Content-Transfer-Encoding; bh=Ns4aRUgWUtil4fiVnvitgeV+q1K/smEYtRGN497S5Ew=; b=Nc2Kzrzas0QqMpWM4fnF5o5wLWlWYFxlGlAipe+85H9cwGgc4hvEKUj1UvgB6I2VHUbJ0OGN/sJO9tjWgwlGypaUuW7Q8x/iI0UtC6cn7X6ZLHT+K6A2A6MdoyR1NF4xxvqPadcmcQwnrY0Tth4ycydpQMlBCZS30sc1qUjUrN0= Received: from [192.168.1.12] (Aurora [192.168.1.12]) by linnabary.us with ESMTPA ; Wed, 12 Apr 2017 13:41:28 -0400 To: ins-a64wsfm3@isnotspam.com From: Admin <admin@linnabary.us> Subject: Welcome to Linnabary Message-ID: <8e8be6cd-6354-aeb9-b577-2b0efc25a1a1@linnabary.us> Date: Wed, 12 Apr 2017 13:41:28 -0400 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101 Thunderbird/45.8.0 MIME-Version: 1.0 Content-Type: text/plain; charset=utf-8; format=flowed Content-Transfer-Encoding: 7bit X-DKIM-Status: invalid (pubkey_unavailable) I honestly have no idea what I should put in here in order to protect myself from filters, so I'm just making it up as I go. - Tad
Source: hmail server – DKIM hmailserver and NameCheap Setup – Stack Overflow



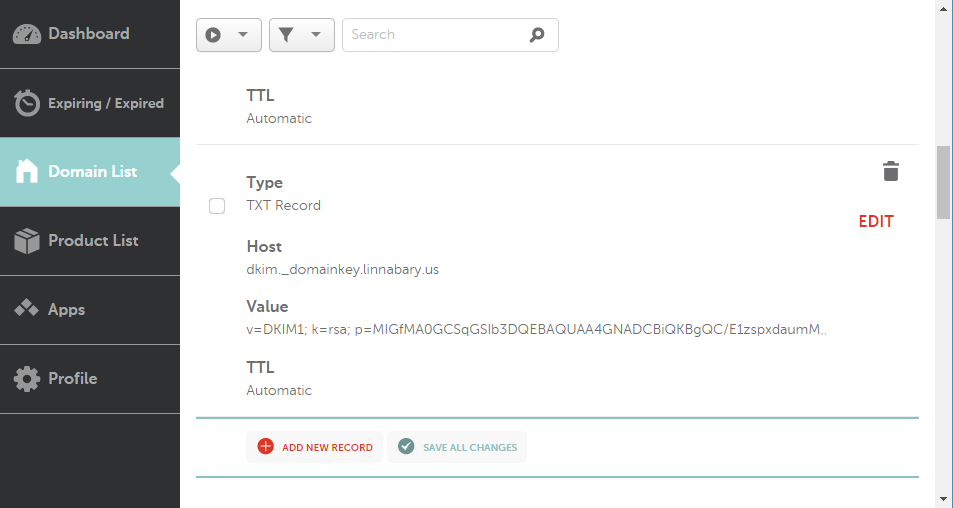
dkim._domainkey.linnabary.us. How does the signature of a test email look? Does it contain the correct domain (d=linnabary.us) and selector (s=dkim)? Also, don’t use online tools to generate secret keys! Useopensslor similar to generate them on your machine. The site you link to sends you a public/private key pair in the response of a POST request. Even if they say they don’t save it, there is no way to check wheather they really don’t, so that key should be seen as compromised already when you get it. – mataApr 12 at 15:33